Top 6 Reasons to Use Multi-factor Authentication
Without Multi-factor authentication protocols, your business insurance MAY be in breach. Multi-factor authentication (MFA) is when you use more than...
3 min read
 Adrian Ghira
:
Updated on August 22, 2024
Adrian Ghira
:
Updated on August 22, 2024

There's much more than passwords at risk when you think about cybercrime today: your reputation, customer trust in your brand, even the well-being of employees can be affected by cyber criminals. Did you know there can even be a risk to your business insurance?
Most businesses use just a username & password to protect what matters most—their data.
Some even went as far as to use two-factor authentication, but in some cases, it's still not enough.
Our lives are filled with multiple devices and we, as users, expect our data to be consistent; synchronized across those devices, from smartphones, to tablets, to desktop computers.
Multifactor authentication is what allows us to make sure that all of our data stays secure, as long as those devices remain in our possession. (ie. no one steals one from you!)
Read on to discover more about multifactor authentication (MFA) and whether it might need to be a part of your IT security policies!
| Table of contents: |
| 1. What is Multi-Factor Authentication? |
| 2. Why Multi Factor Authentication Is Important |
| 3. How does multi-factor authentication work? |
| 4. Pros vs Cons - Multifactor Authentication |
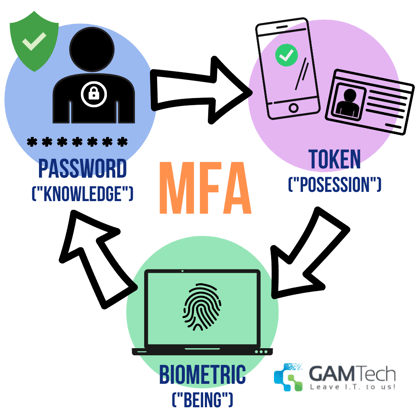
Multi-factor authentication is when you use more than one way to prove who you are when accessing your network. This keeps other people from having access to your data because they do not have all the keys needed to get into your network.
It adds an extra strong layer of security for your business' network, data, and users with a combination of two or more independent pieces of information:
PRO TIP: Some managed security service vendors will claim any combination of two credential types is the same as MFA, but this isn't accurate, you must have 2 out of 3 of the information types above.
Read more: "What Is Two-Factor Authentication"
Think of your iOS or Android device - when you first set up your device, you create some sort of Apple or Google account and a password that you can use to login to that account.
Then when you try to log in, you'll usually get a combination of numbers to enter into your device "to make sure it's you" - this is a security token.
If you use the fingerprint scanner to get access to your phone, tablet, or laptop... you guessed it: this is a biometric verification.
The purpose of having multiple layers of protection is to continue to make things difficult for the potential intruder - if they get a hold of one credential, they still have to go through 2 or more to gain access or to attempt a cyber attack.
We'll go over a basic idea of how the verification process works to keep your data secure later in this post.
The goal of MFA is to create layers of defense that make it more difficult for any cyber criminal to access a target.
What are examples of a target?
Think about all the devices you have in your life.
If they are next to each other but logged into different accounts, someone could steal one device and then have access to everything without any additional steps of authentication.
This is what makes multifactor authentication a necessary step in protecting your business from data breaches and identity theft.
|
The greatest "why?" is one extremely big risk: |
|
Without MFA protocols, your business insurance MAY be in breach. |

Cyber security requirements are becoming an increasingly relevant part of business insurance polices. It is something that most businesses should be talking to their insurance companies, right now.
This is what it looks like in action: when you sign in to your business' network, typically you'll see a small window that pops up requesting another piece of information before logging in.
The information could be sent to a user through an SMS text message sent with a code or token generator software installed on your computer. Once provided, if everything matches up properly, your device will be verified as secure and it will be allowed to access the network.
MFA is not a "set it and forget it" type IT policy, it does require maintenance, updates, and upgrades. Here are some other pros and cons of MFA:
Pros:
Cons:
The good news is that there are several options out there for what kind of multi factor authentication you can choose! Depending on what works best for your small or medium business goals and budget constraints, of course.
If you're looking to implement MFA as a part of your IT policies, you can chat with GAM Tech any time. Book a free consultation right here.

Without Multi-factor authentication protocols, your business insurance MAY be in breach. Multi-factor authentication (MFA) is when you use more than...

Updated October 3, 2021 Once upon a time, a simple login and password was sufficient to keep your valuable business and client data safe. But, just...
-2.png)
In today’s hyper-connected world, businesses rely heavily on technology to drive growth, enhance productivity, and deliver exceptional customer...